Distributed Denial of Service (DDoS)
Distributed denial of service (DDoS) attacks are a subclass of denial of service (DoS) attacks. A DDoS attack involves multiple connected online devices, collectively known as a botnet, which are used to overwhelm a target website with fake traffic.
Unlike other kinds of cyberattacks, DDoS assaults don’t attempt to breach your security perimeter. Rather, a DDoS attack aims to make your website and servers unavailable to legitimate users. DDoS can also be used as a smokescreen for other malicious activities and to take down security appliances, breaching the target’s security perimeter.
A successful distributed denial of service attack is a highly noticeable event impacting an entire online user base. This makes it a popular weapon of choice for hacktivists, cyber vandals, extortionists and anyone else looking to make a point or champion a cause.
DDoS attacks can come in short bursts or repeat assaults, but either way the impact on a website or business can last for days, weeks and even months, as the organization tries to recover. This can make DDoS extremely destructive to any online organization. Amongst other things, DDoS attacks can lead to loss of revenues, erode consumer trust, force businesses to spend fortunes in compensations and cause long-term reputation damage.
DoS vs. DDoS
The differences between regular and distributed denial of service assaults are substantive. In a DoS attack, a perpetrator uses a single Internet connection to either exploit a software vulnerability or flood a target with fake requests—usually in an attempt to exhaust server resources (e.g., RAM and CPU).
On the other hand, distributed denial of service (DDoS) attacks are launched from multiple connected devices that are distributed across the Internet. These multi-person, multi-device barrages are generally harder to deflect, mostly due to the sheer volume of devices involved. Unlike single-source DoS assaults, DDoS attacks tend to target the network infrastructure in an attempt to saturate it with huge volumes of traffic.
Types of DDoS attacks
DoS attacks can be divided into two general categories—application layer attacks and network layer attacks. Each of these types of DDoS attacks define certain parameters and behaviors used during the attack, as well as the target of the attack.
- Application layer attacks (a.k.a., layer 7 attacks) can be either DoS or DDoS threats that seek to overload a server by sending a large number of requests requiring resource-intensive handling and processing. Among other attack vectors, this category includes HTTP floods, slow attacks (e.g., Slowloris or RUDY) and DNS query flood attacks.
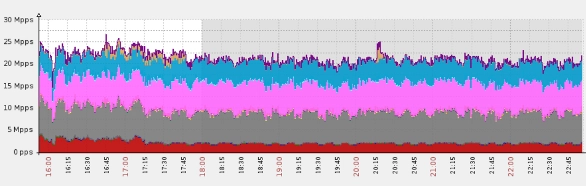
Gaming website hit with a massive DNS flood, peaking at over 25 million packets per second
The size of application layer attacks is typically measured in requests per second (RPS), with no more than 50 to 100 RPS being required to cripple most mid-sized websites.
- Network layer attacks (a.k.a., layer 3–4 attacks) are almost always DDoS assaults set up to clog the “pipelines” connecting your network. Attack vectors in this category include UDP flood, SYN flood, NTP amplification and DNS amplification attacks, and more.
Any of these can be used to prevent access to your servers, while also causing severe operational damages, such as account suspension and massive overage charges.
DDoS attacks are almost always high-traffic events, commonly measured in gigabits per second (Gbps) or packets per second (PPS). The largest network layer assaults can exceed hundreds Gbps; however, 20 to 40 Gbps are enough to completely shut down most network infrastructures.
How to stop DDoS attacks: DIY
You can’t prevent DoS assaults. Cybercriminals are going to attack. Some are going to hit their targets, regardless of the defenses in place. However, there are a few preventive measures you can take on your own:
- Monitoring your traffic to look for abnormalities, including unexplained traffic spikes and visits from suspect IP address and geolocations. All of these could be signs of attackers performing “dry runs” to test your defenses before committing to a full-fledged attack. Recognizing these for what they are can help you prepare for the onslaught to follow.
- Keep an eye on social media (particularly Twitter) and public waste bins (e.g., Pastebin.com) for threats, conversations and boasts that may hint on an incoming attack.
- Consider using third-party DDoS testing (i.e., pen testing) to simulate an attack against your IT infrastructure so you can be prepared when the moment of truth arrives. When you undertake this, test against a wide variety of attacks, not just those with which you are familiar with.
- Create a response plan and a rapid response team, meaning a designated group of people whose job is to minimize the impact of an assault. When you plan, put in place procedures for your customer support and communication teams, not just for your IT professionals.
To truly protect against modern DDoS attacks, you should use a DDoS mitigation solution. Solutions can be deployed on-premises, but are more commonly provided as a service by third-party providers.
Organized by
Dr. M K Prakash
https://www.imperva.com/learn/ddos/denial-of-service/



Comments
Post a Comment